Suppose you want to create a role similar to Analysts, but restrict access to PCI-related reports and queries. Plan a name for the role that describes its function, for example, PCI-Analyst.
Before you begin creating new roles, or application user groups, consider the policies that are required to support the new role. It is a good practice to identify the existing policies that are candidates for use as templates. Under Identities, look for the role that is similar to the one you are planning.
In this example scenario, that role is ug:Analyst. Under Search Policies, check Show policies matching identity, enter the identity, ug:Analyst, and click Go. The policies displayed include those for All Identities and those where ug:Analyst is explicitly named under Identities.
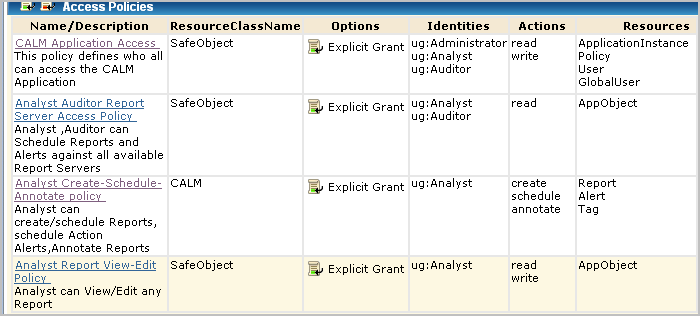
The policy names that include this role follow:
For each of the candidate policies, examine the definition and determine which of the following actions to take:
This action is appropriate for the following policies in this example:
This action is appropriate for the following policy in this example, where the new copy would include only the new identity and would have an additional filter to limit the read/write access to reports tagged PCI:
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |