Before you create policies for a given user or application user group, log on as that user or group member and determine what you can and cannot do. First, verify that the restrictions you expect to be in place are working. Second, verify that you can perform the tasks you expect such users to do.
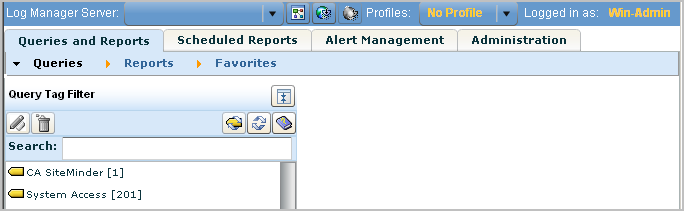
For this scenario, you expect to be able to view only reports or action alerts that are tagged with System Access. In the example, the only available query tag filter is System Access. Therefore, the expectation is verified.
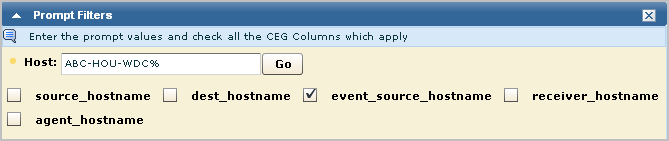
A quick way to test an access filter is to use the Prompts function. However, this function is not available to the Win-Admin user. All the prompt queries have the tag "Event Viewer". Access to Prompt Filters can be granted with the policy filter calmTag=Event Viewer.
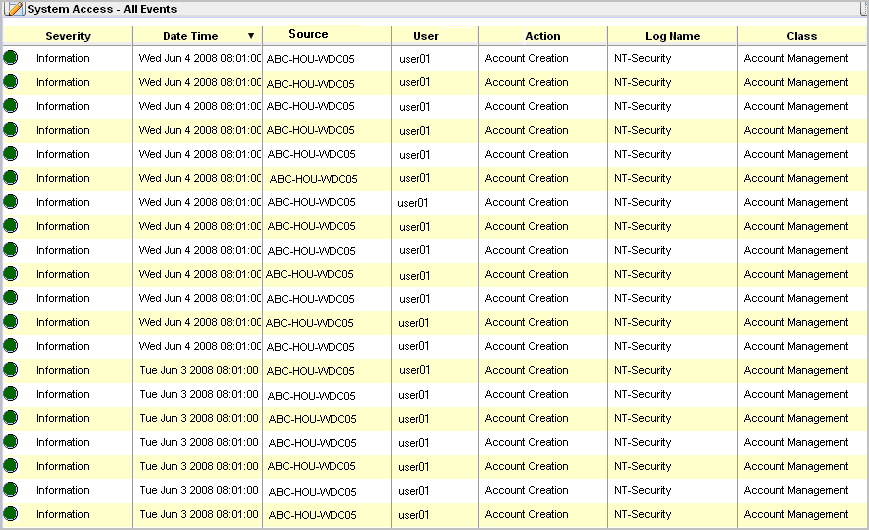
The best way to test an access filter is to review the data displayed on a report. Consider the following access filter. The event_logname CEG column begins with NT- and the CEG column event_source_hostname begins with ABC-HOU-WDC, an abbreviation for the ABC company, Houston location, Windows Domain Controller.
event_logname Like NT-% AND event_source_hostname Like ABC-HOU-WDC%
The following example shows a report viewed by the user to whom this access filter applies. Notice the data in the Log Name column begins with NT- and the data in the Source column begins with ABC-HOU-WDC.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |