When you create an access policy for CALM or a scoping policy, you select one of the following three types:
This choice impacts the level of detail for access policy configuration, where access policy is the broadest.
Note: The examples shown here are access policies for the CALM resource class and therefore, include actions and resources specific to CA Enterprise Log Manager.
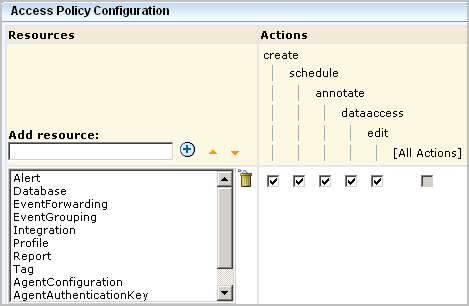
An access policy specifies actions that are valid for any of the selected resources that are granted to all selected identities. When you create a generic policy for CA Enterprise Log Manager, you add resources belonging to the CALM resource class, and then you select actions from the displayed list. The actions you select apply to the selected resources for which they are valid. In this example, the policy allows each selected action to be performed on all the selected resources for which create is valid.
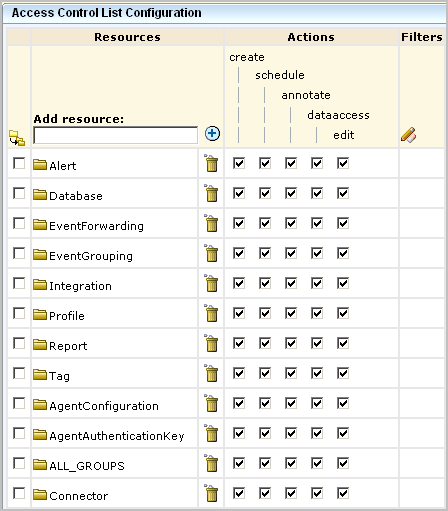
An access control list specifies actions valid for each resource separately for the selected identities. When you create a resource-centric policy, you specify what actions are permitted on each resource. You do not need to select actions for a given resource simply because they are valid. For example, you can allow create for reports but not allow create for alerts, even though create is a valid action for alerts. The access control list is the most fine-grained policy when it is implemented for one identity at a time.
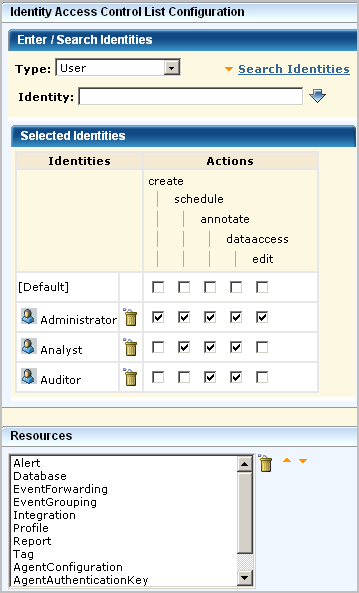
An identity access control list specifies the actions granted to selected identities for all applicable selected resources. When you create an identity-centric policy, specify which identities can perform which actions (create, schedule, annotate, edit) on all the listed resources to which each action applies. If you want to restrict the Auditor from scheduling alerts, you would leave schedule blank. However, leaving schedule blank would also restrict the Auditor from scheduling reports.
| Copyright © 2011 CA. All rights reserved. | Email CA Technologies about this topic |